Last Updated on October 2, 2024 by One Nation Under Arrest | Admin
Being true to the pattern of training, most operations will have some form of guidelines, some rules of engagement at the minimum. There have been several Federal programs that have launched heavily funded infiltration tactics on different social, racial, and political groups since domestic intelligence gathering began with J Edger Hoover, the head of the F.B.I. in the 50’s, when they surveilled the general populace looking for Russian spies, and soviet sympathizers. That was their guise anyway.
“Centralized operations under COINTELPRO officially began in August 1956 with a program designed to “increase factionalism, cause disruption and win defections” inside the Communist Party U.S.A. (CPUSA). Tactics included anonymous phone calls, IRS audits, and the creation of documents that would divide the American communist organization internally.[11] An October 1956 memo from Hoover reclassified the FBI’s ongoing surveillance of black leaders, including it within COINTELPRO, with the justification that the movement was infiltrated by communists.[12] In 1956, Hoover sent an open letter denouncing Dr. T.R.M. Howard, a civil rights leader, surgeon, and wealthy entrepreneur in Mississippi who had criticized FBI inaction in solving recent murders of George W. Lee, Emmett Till, and other blacks in the South.[13] When the Southern Christian Leadership Conference (SCLC), an African-American civil rights organization, was founded in 1957, the FBI began to monitor and target the group almost immediately, focusing particularly on Bayard Rustin, Stanley Levison, and, eventually, Rev. Martin Luther King, Jr.[14]”
Fast forward almost 70 years into the future and there is not only a vast Military Industrial Complex of private companies bidding for government contracts to build war machines for air, land and sea. There are also DoD, DIA, and DoJ contracts going towards private companies that build electronic systems that will capture, retrieve, store, copy, clone, image, duplicate, filter and process any person’s data who is on or offline.
The largest of these firms collecting ALL of our data, used to employ the now famous Edward Snowden, who was brave enough to inform the population of the facts of their actions, leading to his political exile, currently in Russia.
“The consulting firm, which derives nearly all of its revenue from government agency contracts, disclosed in June that it is under both criminal and civil investigation by the DOJ for how it calculated costs billed to the U.S. government.” – Booz Allen Hamilton says Justice Department probe could take years to resolve
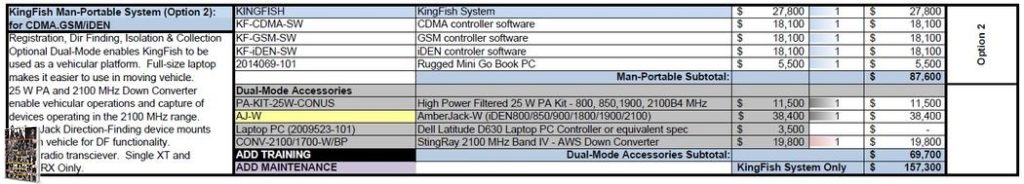
One of the most common unlawful methods of electronic data from a group at any location, static or mobile, is the Stingray fake cell tower, made by Harris. This method has been utilized for about 20 years in the United States in different forms but the latest design has made it affordable and accessible to use in large cities with war protestors, rights activists and overall government defectors.
“It seems that the devices are often sold in packages, like the StingRay II (a more powerful, updated version of your typical StingRay) Vehicular System. This comes with equipment for operating a StingRay from a patrol vehicle and three different kinds of Harris’ Harpoon signal amplifiers. A laptop, three kinds of software for accessing different types of cellular networks, and an AmberJack cell phone tracker are also included for a grand total of $148,000. ” – Here’s How Much a StingRay Cell Phone Surveillance Tool Costs
The most common way to capture the data from a person’s life is to make the average online experience a social one, make it free, easy to use, and popular, and the average person will provide their most intimate details with the world through selfies and descriptions thereof.
We now provide Terabytes of information on a daily basis to a social network that in turn creates a profile that has value to both private and government sectors. Few companies monopolize this industry like the facebook does.
“At Facebook, we have unique storage scalability challenges when it comes to our data warehouse. Our warehouse stores upwards of 300 PB of Hive data, with an incoming daily rate of about 600 TB. In the last year, the warehouse has seen a 3x growth in the amount of data stored. Given this growth trajectory, storage efficiency is and will continue to be a focus for our warehouse infrastructure.” – Scaling the Facebook data warehouse to 300 PB
In the aftermath of the Twin Peaks Ambush, there is a federal operation in place that specifically reaches into the social network lives of bikers and those who support them. This effort is focusing in on the “protestors,” and the way in which the entire motorcycle community was going to protest or react to this “ambush on a political meeting,” as well as find connections to “would be persons of interest” that would be necessary to try and prosecute the political entity target.
This evidence would be necessary when prosecuting a large organization such as an MC. The investigation is led by the Department of Homeland Security, and although the name of the operation is not yet known, the existence has been experienced first hand.
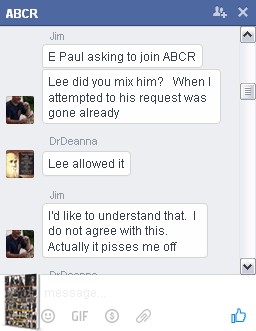
The main organizer of this information is a Mesquite, Texas fireman, and trained DHS agent. James Baldwin, or “Jim” as he asks to be called, rallied several family members who were affected by the Twin Peaks tragedy and placed them in “chat rooms” and closed pages on social media to discuss the events of the day, as well as the lead up to the event. Baldwin worked closely with or for, the Looney & Conrad Law firm with weekly reports of intelligence gathered from online sources.
Interesting enough after James Baldwin read his name in this chapter, he called out the author by name, seemingly upset.
Danielle Bundy Luther, Richard “Lexx” Luther’s supposed wife, text Lexx on May 17, 2015 that she was “going to ride with Sassy to Waco to pick up Bill.” Presumably William Flowers (AKA Bill, Billy, Cossack Stone Cold). It was William Flowers who invited Richard Luther and his riders to Twin Peaks, not a member of the Red and Gold MC. Very vocal group of people. Flowers’ interview with FBI Agent Skillstead revealed that of the 1,300 Cossacks in Texas, 20 of the riders are known Law Enforcement Officers from “Ft. Worth Police Department to Harris County S.W.A.T.”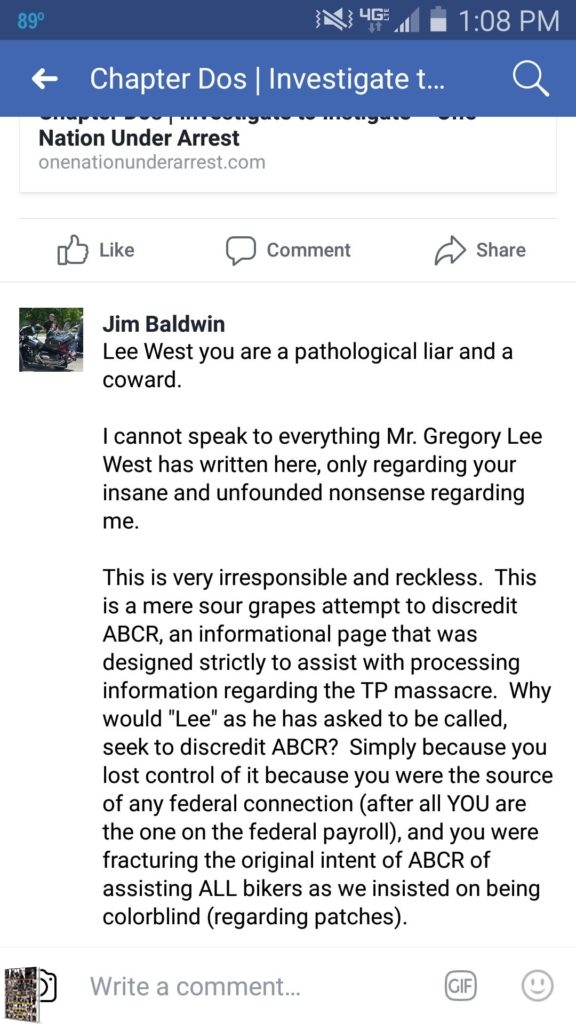
For those of you who have yet to read the About the Author section of this book, here is the authors information. As a disabled Veteran, garnering a “federal” paycheck for disabilities acquired during service, Agent Baldwin is half correct in his assumption that the author is federally connected to anything in this tragedy, however he is absolutely lying about his (Agent Baldwin’s) role in the aftermath of Twin Peaks.
It was Agent Baldwin who introduced Rich Luther to the author, and it was Agent Baldwin who tried to get the author to provide $40,000 worth of plant material to Lexx in December of 2015 whilst in Colorado. Agent Baldwin used the “colorblind” line often when defending the Cossacks actions before and after Twin Peaks. Yet he was adamant that NO R&G were added to the closed room group. Baldwin gave Admin status to the author when Baldwin’s relationship with Roxanne Avery was being questioned by her boss and sometimes boyfriend, Paul Looney, as well as her husband.
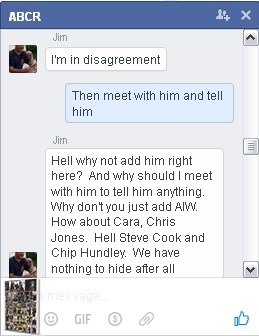
The sway of the conversation and domination there of, after the fact, was necessary for all of the federal organizations involved that needed a slight of hand to magically disappear from the conversation and be void from the average protestors mouth and of course, not appear in any news media, local or national.
The Federal Communications Commission would never allow their enforcement branches to look bad in public. So the task of cleaning up a huge train wreck of an undercover operation was left to the “local yocals” to figure out, yet with the help of the press, and the Department of Justice, it would be possible.
“Sink Swanton” was a talking point in the protests, instead of “Arrest McCraw.” Keep the conversation local in focus, which deserves as much attention as it can get, but the protestors barely mentioned larger entities such as the DoJ, DoD, DIA, NCC, DHS, DEA, FBI, BATFE, TABC, Texas Parks and Wildlife or DPS, all of whom where present in some form or fashion on May 17th, 2015.
Almost pointless to say, but “no one blamed the FCC for airing such blatant lies during the coverage of the tragic event and the horrific aftermath.” For the last 6 months of 2015, the focus on the tragedy was on two attorney’s strategies for the defense of less than a dozen victims, and even a few aggressors in the situation.
NOTE: Both of those outspoken attorneys were representing both sides of the tragedy:
Clint Broden represents the Scmimtars, lead by a former Son’s of the South biker, which would make him a former C.o.C. & I. Member, Matthew Clendennan. Broden also represents a C.o.C. & I. biker from the Dallas area, both of his clients were indicted, Clendennan was indicted for a second time on August 16th, 2017.
Paul Looney, from Houston, was representing two bikers who were not indicted from the C.o.C. & I. as well as a Cossack who was indicted twice. This Cossack gave a graphic fictional story to the press about how his step-dad was murdered in front of him by members of the C.o.C. & I.. Cossack Cody Ledbetter, not to be confused with DPS Sgt. Cory Ledbetter, opened up to the public for sympathy when he gave a first hand account how his step-dad was murdered point blank. Latter ballistics would show that the bullets that entered Boyett’s skull were from Law Enforcement automatic weapons, one bullet likely from WPD S.W.A.T. Michael Bucher and one bullet from one of the two DPS agents shooting from Don Carlos patio, likely DPS Sgt. Cory Ledbetter. Ironic?


Q: How does the legal system continue to rule and control the general population?
Analogy: Suppose we flipped a coin to decide who gets to spend tax dollars. Two possible outcomes if one party chose heads, while the other got tails. One outcome is only possible if in reality both parties were answering to a larger group who owns the actions of either group. In this analogy the larger group who owns both parties actions is the Department of Justice controlled by the American Bar Association. Any wonder why FBI agents have to pass and maintain a passing grade on a BAR exam each year to maintain their agent status?
If patterns are to be noticed the narrative would be: “Make sure the media will only pay attention to local court procedures that will never be fruitful, all the while the Department of Justice continues on with mission as planned.” With a likely mission statement directed to DHS as: “Observe and report all interactions between clubs and those supporting them.”

The following excerpt is from an insightful whitepaper written for the Pew Foundation, and the New American Century, (think tanks for lobbyists and large corporations, such as ammunition manufacturers, prison construction companies, the prison industry, and the military industrial complex as a whole.) The following extended quote might have been used as guidelines on how to instigate, rather than deconfliction as the author intended.
The focus is on a series of Federal Investigations into “patriot type” movements from the 80’s until around 2005, namely Operation PATCON. The 1993 time frame is important to note during the timeline of events when the first Waco tragedy took place where the same entities above collided right outside of town near Mt. Carmel, Texas. The entire 40+ pages is worth the time to read as it mentions federal agencies not knowing each other had undercover agents or high level informants in certain positions and they fed each other crime and blamed it on the groups they were surveilling. If history repeats itself, then the B.A.T.F.E. will show up in the center of the Twin Peaks Ambush, and too bad for the victims, the B.A.T.F.E. is who is in charge of ballistics.
Recommendations
“The PATCON case study points to the need to gather more data on the secondary effects of infiltration and to manage the use of this tool more responsibly. Areas for further study and additional government disclosure include:
An independent examination of the FBI’s statistical scoring system for evaluating field office performance, with an eye toward measuring how the frequency of use of extraordinary tools such as Foreign Intelligence Surveillance Act (FISA) warrants and undercover operations compares to the frequency of prosecutions resulting from such investigations.This should not be seen as marshaling evidence against the use of extraordinary tools, but the number of completed prosecutions is a valid and useful data point in this discussion. The statistical scoring system should also be evaluated as to whether it creates artificial pressure to use infiltration and other extraordinary techniques apart from a legitimate investigative interest. A quantitative study of the long-term use by federal agencies of confidential sources (informants) and undercover operations that have been publicly disclosed.
This study should identify useful data for comparison and analysis, such as the length of infiltration, the number of agents and informants per target, the number of targets covered by each agent and informant, the tactics used to infiltrate, conviction rates, and judicial rulings on the admissibility of informant and undercover testimony. The study should also define and quantify the types of confidential sources used, since these can range from a one-time report of suspected misdoings to extended surveillance by paid informants.
Use of the Freedom of Information Act to create additional detailed case studies of historical infiltration operations that have not been fully and publicly disclosed, with special attention to violent extremism cases with significant risk of alienating or radicalizing feedback in targeted communities.
Detailed polling and focus groups to collect data on how infiltration is perceived in both targeted communities and control groups, with an eye toward understanding the secondary effects of infiltration and how they affect public trust in government and willingness to cooperate with law enforcement. Case studies on the use of informants and undercover operations by local law enforcement agencies in different jurisdictions, where many of the same issues apply. Compare and contrast these examples with federal programs.
Additional study should proceed with a clear understanding that infiltration is an important tool for law enforcement, but one that poses unique challenges in direct proportion to its unique capabilities. Such study should be undertaken by strictly neutral parties rather than advocates, since the volume and nature of the data make it easy to selectively mine information in support of a per-determined conclusion. The extreme complexity and political volatility of the issues that arise from infiltration programs create an unusually high risk of such confirmation bias.” – J.M. Berger, May 2012 National Security Studies Program Policy Paper – PATCON – The FBI’s Secret War Against the ‘Patriot’ Movement, and How Infiltration Tactics Relate to Radicalizing Influences
“We have investigated ourselves and found that we have done nothing wrong, and we need more money. “ Texas Department of Public Safety Public Information Officer Tom Vigner, March 2015.
This satire quote by the author can easily explain much of what took place in the investigation that would happen in May regarding the DPS involvement of their infiltration of the C.o.C.&I. meeting at Twin Peaks. April of 2015 just so happens to be when DPS became in charge of investigating public corruption in Texas (including Law Enforcement), instead of the special commission formed through the District Attorney’s office of Travis County.
“In 2013, she was arrested for and pleaded guilty to drunk driving. She was sentenced to forty-five days in jail.[5] According to Lehmberg’s lawyer, David Sheppard, Lehmberg’s sentence was “without doubt the harshest sentence anyone has ever received for first time DWI” in Travis County.[6] Video of her detainment and extremely inebriated and aggressive behavior was released to the public. Governor Rick Perry demanded Lehmberg’s resignation, and stated that if she did not step down, he would use his line-item veto power to cut all funding to the Public Accountability Office which is under Lehmberg’s authority. Lehmberg refused, and Governor Perry vetoed the office’s funding. Perry was indicted for this action but was later cleared of all charges.”
She had a logical case against Perry, and the state of Texas would have been in for a rude awakening from the evidence, but her infraction got more publicity than his. FCC strikes again.
Texans almost got hope for a reprieve from this police state abuse in 2017, but funding was never appropriated for a renewed Public Integrity Unit by the District Attorneys office of Travis County.
“Now under new management, the Travis County district attorney’s office is trying to restore some muscle to its Public Integrity Unit after a Republican backlash led to deep funding cuts and limitations on the unit’s duties.
Under District Attorney Margaret Moore, who took office in January, negotiations with Gov. Greg Abbott’s office and key lawmakers paid off when the proposed House budget, introduced earlier this year, set aside $4.8 million for the unit.
But the budget approved this week by the Senate included no money for the Travis County division, raising doubts about plans to beef up the unit’s investigations and prosecution of insurance scams and fraud committed against state agencies or by state employees.” – Travis County eyes restored Public Integrity Unit
Has anyone taken the time to question how any leadership in government, or even media themselves can claim any news source is “Fake News?” They are all governed by the same Federal Communications Commission, and the broadcasting company airing the fake words would have their license revoked for broadcast if the government did not want it stated. Enter “free speech” and you have an interesting coin that is presented to the audience en masse.